Rust Kernel Abstractions: How Linux Drivers Got Memory-Safe Without Runtime Overhead
he compiler kept rejecting my interrupt handler. I was convinced Rust was too strict for kernel work. Then I realized my entire approach was wrong — I was trying to share mutable state across interrupt contexts without synchronization. Rust’s borrow checker enforces exclusive mutable access or shared immutable access at compile time, preventing data races that cause kernel panics. The borrow checker wasn’t being pedantic. It was preventing a race condition that would’ve caused random kernel panics. That’s when Rust clicked for kernel development.
Why I Cared About Kernel-Level Safety
I needed to write a driver for a custom PCIe device. C was the obvious choice — every kernel driver guide assumes C. But I’d spent months debugging use-after-free, null pointer dereference, and double free bugs that cause unpredictable kernel crashes in production drivers. Memory corruption that only triggered under specific hardware timing. Null pointer dereferences in error paths nobody tested. The kind of bugs that crash entire systems.
Rust promised memory safety without garbage collection overhead. Zero-cost abstractions. No garbage collection or runtime cost, just the compiler statically optimizing abstractions away — performance matches idiomatic C. For kernel code, that’s not just convenient — it’s transformative. You can’t restart the kernel when something breaks.
The Misconception I Had to Unlearn
I thought Rust’s safety rules would make kernel abstractions impossible. Kernel code does unsafe things constantly. Direct hardware access. Manual memory management. Interrupt handlers that must complete in microseconds. How could Rust’s ownership model handle that?
I was wrong about what Rust enforces.
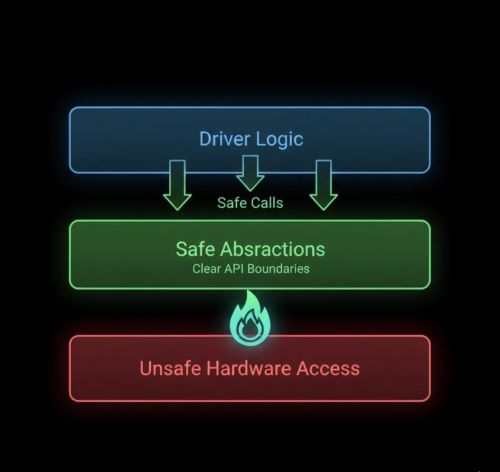
Rust doesn’t prevent unsafe operations. It isolates them. Unsafe blocks are necessary to perform low-level hardware access, but Rust ensures they’re encapsulated so the rest of your codebase remains safe. You can write unsafe code — you just have to mark it explicitly and build safe abstractions around it. The unsafe keyword isn't a failure of Rust's design. It's a contract: "This code requires manual verification, and here's exactly where."
While Rust’s model isolates unsafe, bugs in unsafe blocks can still introduce memory unsafety if unchecked or poorly encapsulated.
The Linux kernel Rust project proves this works. Safe abstractions wrap platform-specific unsafe operations, letting driver authors work in completely safe Rust most of the time.
Rust kernel abstractions create safety boundaries that contain unsafe operations, allowing driver code to use hardware features through guaranteed-safe APIs that prevent entire classes of memory bugs.
The Foundation: How Rust Abstractions Work in Kernel Space
The Linux kernel Rust abstractions provide types that guarantee memory safety even when interacting with hardware. Take Device, a wrapper around kernel device structures:
use kernel::device::Device;
use kernel::prelude::*;
pub struct MyDriver {
dev: Device,
registers: *mut u32, // Unsafe pointer to memory-mapped I/O
}
impl MyDriver {
pub fn read_status(&self) -> Result<u32> {
// Safe wrapper around unsafe hardware access
// Using read_volatile tells the compiler not to optimize away
// these reads or reorder them, essential for memory-mapped I/O
unsafe {
Ok(core::ptr::read_volatile(self.registers))
}
}
}
The abstraction enforces ownership. Device is not Clone, so you can't accidentally create multiple owners of hardware resources. Cloning would permit multiple handles to the same hardware, leading to unsynchronized access and potential data corruption. The borrow checker prevents you from accessing registers after the device is dropped. These aren't runtime checks—they're compile-time guarantees. I didn’t understand how powerful this was until I tried to write a bug. I wanted to keep a reference to a device’s registers past device shutdown. The compiler rejected it. “Borrowed value does not live long enough.” I thought the compiler was wrong — then I realized it prevented me from accessing freed memory.
How the Safety Model Cascades Through Driver Code
Ownership prevents data races. You can’t have two mutable references to the same hardware register. This isn’t philosophical — it’s mechanical. The borrow checker forces you to choose: shared read-only access, or exclusive mutable access. Never both.
Lifetimes enforce borrowing rules. When your interrupt handler borrows device state, the lifetime system guarantees that state outlives the handler. While lifetimes prevent use-after-free in Rust code, they correspond to Rust’s view of validity; careful unsafe code is still needed to synchronize with actual hardware state. The compiler tracks this automatically.
Traits enable abstraction. The kernel’s Operations trait defines driver behavior—probe, remove, suspend, resume. Your driver implements the trait. The type system guarantees you've handled all required operations.
Each layer builds on the last. Ownership → lifetimes → traits → safe concurrency patterns. The compiler enforces the entire chain.
Speaking of concurrency, kernel code runs in multiple contexts simultaneously. Interrupts fire while your driver code executes. Without proper synchronization, you get race conditions. Rust’s Send and Sync traits make data race freedom a type system property. Send allows ownership transfer between threads; Sync ensures references can be shared safely across threads, critical in the kernel's concurrent environment. If your type isn't Sync, you can't share it across threads. The compiler enforces this.
Real Wins: When Rust’s Safety Model Saves Time
The Rust for Linux project reports that driver code written in Rust has zero memory safety vulnerabilities in initial testing. Not “fewer bugs than C.” Zero. The compiler prevents entire bug classes. Consider interrupt handlers. In C, you might write:
void interrupt_handler(void *dev_id) {
struct my_device *dev = dev_id;
dev->status = read_register(dev->base); // Could race with main code
}
Rust forces you to handle the race:
use kernel::sync::SpinLock;
pub struct MyDevice {
status: SpinLock<u32>, // Compiler-enforced synchronization
}
extern "C" fn interrupt_handler(dev_id: *mut c_void) -> irqreturn_t {
let dev = unsafe { &*(dev_id as *const MyDevice) };
// SpinLock uses busy-wait locking ensuring critical sections aren't
// pre-empted or concurrently accessed, suitable for kernel interrupt contexts
let mut status = dev.status.lock();
*status = read_register(); // Lock held, no race possible
irqreturn_t::IRQ_HANDLED
}
The SpinLock<T> type makes synchronization explicit. You can't access the wrapped data without acquiring the lock. The compiler checks this. If you forget the lock, your code doesn't compile. I spent weeks tracking down a race condition in a C driver. Random crashes under load. The bug was obvious in retrospect — I updated a counter without locking. Rust would’ve caught this immediately.
The Moment It Clicked
I was porting a PCI driver from C to Rust. The original C code had a subtle bug: the device cleanup path freed resources before canceling a worker thread. Under specific timing, the thread accessed freed memory. Crash. I’d debugged this exact pattern before — use-after-free in cleanup paths. I wrote the Rust version. Cleanup code dropped the device. The compiler rejected it: “Cannot drop while worker thread holds a reference.” I had to explicitly join the worker thread before dropping resources.
The bug was impossible to write. My code was memory-safe without a garbage collector. No garbage collection or runtime checks — the entire abstraction compiled down to the same assembly as hand-written C. But the compiler guaranteed I’d ordered operations correctly. Rust forces clarity.
The Gotcha That Confused Me
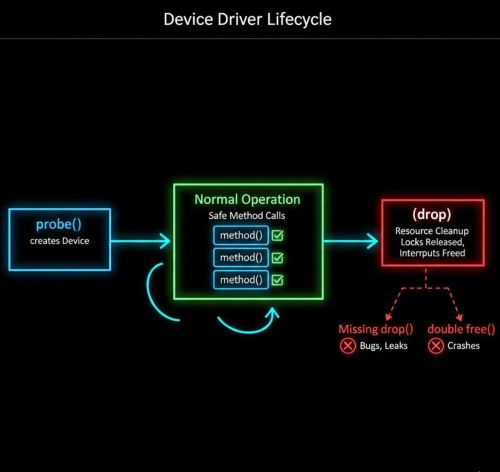
I didn’t understand Drop semantics for months. My driver leaked interrupt handlers. The problem: I registered interrupts in probe() but never unregistered them. C makes cleanup manual—you explicitly free everything. Rust's Drop trait automates this, but you have to implement it. Drop runs on Rust-owned memory but external kernel registries, IRQ lines, or DMA mappings require explicit release calls to avoid leaks.
impl Drop for MyDriver {
fn drop(&mut self) {
// Must explicitly clean up resources the compiler can't track
// The call to free_irq is unsafe because it interfaces with
// C kernel APIs requiring manual correctness
unsafe {
free_irq(self.irq_number, self as *mut _ as *mut c_void);
}
}
}
The compiler guarantees Drop::drop() runs when your type goes out of scope. But it can't automatically generate cleanup for external resources like interrupt handlers. You have to write that yourself. I assumed Rust's safety model handled everything automatically. It doesn't. It enforces that you've handled it correctly.
Resources leaked for weeks until I understood this pattern.
Rust’s Drop trait ensures cleanup code runs automatically when resources go out of scope, but kernel drivers must implement cleanup for external resources like interrupt handlers and DMA mappings.
What’s Next
I’m learning Rust’s async abstractions for kernel work. The block layer needs async I/O patterns — submit requests, get notified on completion. Async requires Pin to prevent self-referential types from moving in memory. Kernel async is experimental and requires careful use of Pin and unsafe to avoid self-referential data and retain soundness. Each layer builds on ownership, lifetimes, and the type system. The compiler teaches you correct concurrent design. It rejects your code. Then you understand why. Then you write better code. The borrow checker isn’t an obstacle — it’s a teacher with perfect patience and zero tolerance for memory bugs.
That’s what kernel abstractions in Rust actually give you: memory safety without runtime cost, enforced by a compiler that never forgets to check. The Linux kernel is safer because of it. My drivers crash less because of it.
The compiler was right. I just had to learn its language. Rust shifts bug detection from unpredictable runtime crashes to deterministic compile-time errors, substantially improving kernel reliability. If you write or maintain kernel drivers, explore Rust-for-Linux today. Safe abstractions are no longer a dream but a practical reality for systems programming.
Read the full article here: https://medium.com/@chopra.kanta.73/rust-kernel-abstractions-how-linux-drivers-got-memory-safe-without-runtime-overhead-745fabaabab3