Safe-by-Design n8n for SaaS: Multi-Tenant Automation That Scales
Learn a secure multi-tenant n8n architecture for SaaS: isolation models, secrets, RBAC, rate limiting, queueing, audit, and upgrade strategy — plus code and diagrams.
Let’s be real: customers don’t just want automation — they want automation they can trust. If your SaaS runs n8n for each client’s workflows, a leaky boundary or noisy neighbor can end a deal fast. Here’s a pragmatic blueprint to ship multi-tenant n8n that’s boringly secure and pleasantly scalable.
The Core Problem n8n is fantastic for building workflows, but it isn’t a turnkey multi-tenant product. You have to make deliberate choices about isolation, secrets, and scale. The goal: give every customer autonomy without letting them affect anyone else — on performance, security, or cost.
Choose Your Isolation Model (and Be Honest About Trade-offs) There are three patterns most teams land on: 1) Per-Tenant Stack (Strongest Isolation)
- What: One n8n instance (and DB/queue namespace) per tenant, fully isolated via containers or VMs.
- Pros: Best security boundary, simplest incident blast radius.
- Cons: Operational overhead for hundreds of tenants.
Use when: Enterprise customers, regulated data, high variance in workload. 2) Shared Control Plane, Isolated Execution (Balanced)
- What: A shared admin plane (provisioning, auth, billing) with per-tenant n8n workers, DB schemas, and queues.
- Pros: Strong isolation for runtime and secrets; centralized management.
- Cons: More moving parts than single pool.
Use when: Mid-market/enterprise mix, predictable growth. 3) Shared Pool (Lightest)
- What: Single n8n cluster; tenants are rows in the same DB; logical isolation via RLS (Row-Level Security) and per-tenant encryption keys.
- Pros: Easiest to operate; best density.
- Cons: Highest lateral-movement risk if misconfigured; noisy neighbors.
Use when: Low-risk data, early stage, or internal tenants.
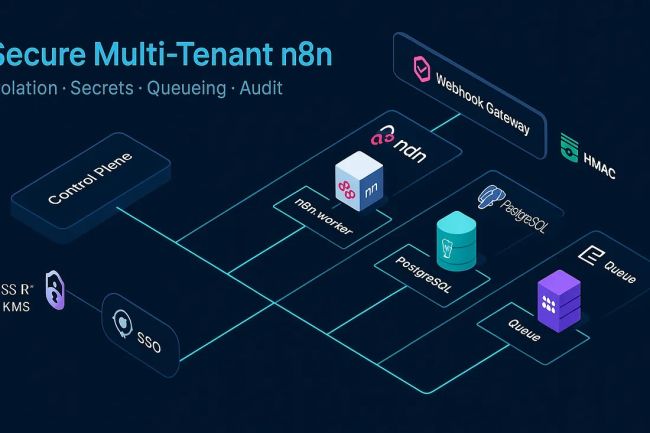
Reference Architecture (Shared Control Plane + Isolated Execution)
+---------------------------+
| SaaS Frontend |
+-------------+-------------+
|
v
+------------------+ +------+------+
| Identity (SSO) |-->| Control |
| OIDC/SAML/JWT | | Plane |
+------------------+ | (API/Billing|
| Provision)|
+------+------+
|
+--------------+-----------------------+
| |
v v
+-------+--------+ +------+--------+
| Tenant A | | Tenant B |
| n8n Workers | | n8n Workers |
| DB schema: A_* | | DB schema: B_*|
| Queue: a-_* | | Queue: b-_* |
+-------+--------+ +------+--------+
| |
v v
+-----+-----+ +-----+-----+
| Webhook | | Webhook |
| Gateways | | Gateways |
+-----+-----+ +-----+-----+
Shared but namespaced: object storage, secrets KMS, metrics, logs, and audit.
Key ideas:
- Provision each tenant a dedicated worker pool, DB schema, and queue namespace.
- Use a gateway layer for webhooks to terminate TLS, verify tenant JWTs, and enforce rate limits before traffic reaches n8n.
Data Boundaries: Database, Queue, Storage Database
- Prefer PostgreSQL with one schema per tenant (e.g., a_*, b_* tables) or separate DBs for top-tier accounts.
- Enable Row-Level Security if you must share tables, and enforce tenant_id via session settings.
-- Example: enforce tenant isolation with RLS
ALTER TABLE workflow_executions ENABLE ROW LEVEL SECURITY;
CREATE POLICY tenant_isolation ON workflow_executions
USING (tenant_id = current_setting('app.tenant_id')::uuid);
-- On connection (per worker):
SELECT set_config('app.tenant_id', :tenant_id, false);
Queueing
- Use a queue per tenant (a-jobs, b-jobs) to prevent noisy neighbors.
- Assign worker concurrency per tenant to respect SLAs.
Object Storage
- Partition by tenant prefix (e.g., s3://n8n-prod/tenant-a/...).
- Apply bucket policies and KMS encryption with per-tenant keys where feasible.
Webhook Security and Throttling Place an API gateway or reverse proxy in front of n8n webhooks:
# Tenant-aware webhook gateway (sketch)
server {
listen 443 ssl;
server_name hooks.example.com;
# TLS config...
location /t/(?<tenant>[a-z0-9-]+)/ {
# 1) Authn via JWT (from your SaaS)
auth_jwt "Tenant Access";
auth_jwt_key_file /etc/keys/jwks.json;
# 2) Rate limit per tenant
limit_req zone=tenant_$tenant burst=50 nodelay;
# 3) Route to the right n8n workers
proxy_set_header X-Tenant-Id $tenant;
proxy_pass http://n8n-$tenant;
}
}
- JWT includes tenant_id, plan, and scopes. Expire tokens aggressively.
- Rate limiting prevents abuse and protects downstream nodes.
Secrets, Credentials, and Environment Strategy
- Use an external KMS/secret manager (AWS KMS + Secrets Manager, GCP KMS + Secret Manager, or Vault).
- n8n credentials should be stored encrypted, but treat the n8n DB as “encrypted but recoverable”; ultimate trust lives in your external KMS.
- Rotate credentials automatically — especially OAuth refresh tokens — and capture rotation attempts in audit logs.
- Separate config (env vars) from secrets (KMS). Avoid baking secrets into images.
Identity & Authorization
- SSO first: OIDC/SAML for tenant admins; SCIM if you want to sync users/roles.
- Map SaaS roles to n8n permissions using RBAC: who can edit workflows, view logs, or manage credentials.
- For public webhooks, require HMAC signatures (e.g., X-Signature) validated at the gateway. Reject if missing or skewed timestamps.
Execution Safety: Sandboxing and Egress Controls
- Run n8n workers in containers with read-only filesystems, seccomp/AppArmor, and non-root users.
- Lock down egress with per-tenant outbound allowlists (e.g., only call declared APIs).
- For custom code nodes, set resource limits (CPU/memory) and timeout ceilings.
Observability, Audit, and Forensics
- Per-tenant dashboards: executions/min, success rate, P95 latency, retries, queue depth.
- Audit trails: who changed a workflow, who updated credentials, which webhooks were invoked.
- Log the effective tenant_id on every request and execution. Ship to a central log index with a tenant field for rapid incident slicing.
Upgrades Without Drama
- Maintain an immutable image per tenant channel: n8n:24.6-tenant-a.
- Use canary promotions: upgrade a low-risk tenant first, observe, then batch-promote.
- Version workflows: store definitions in Git (via n8n’s export or your own tooling). Rollbacks should be one click, not a prayer.
Sizing & Cost Controls
- Give each tenant a concurrency budget and execution quota tied to their plan.
- Scale worker replicas horizontally on queue depth or execution lag.
- Kill runaway jobs with max attempts and dead-letter queues (DLQs) for post-mortems.
Example: Minimal Per-Tenant Worker (Docker Compose)
version: "3.8"
services:
n8n-a-worker:
image: n8nio/n8n:latest
command: n8n worker
environment:
- N8N_ENCRYPTION_KEY=${TENANT_A_ENC_KEY}
- DB_POSTGRESDB_HOST=pg
- DB_POSTGRESDB_DATABASE=n8n
- DB_POSTGRESDB_USER=n8n
- DB_POSTGRESDB_SCHEMA=a_schema
- QUEUE_BULL_REDIS_HOST=redis
- EXECUTIONS_MODE=queue
- N8N_DIAGNOSTICS_ENABLED=false
- N8N_SECURE_HEADERS=true
read_only: true
user: "1001:1001"
depends_on: [pg, redis]
deploy:
resources:
limits:
cpus: '1'
memory: 512M
Pair this with per-tenant Redis namespaces and Postgres schemas to keep jobs and data cleanly separated.
Real-World Example (Condensed) A B2B SaaS running 200+ tenants moved from a shared n8n cluster to the shared control plane + isolated workers model:
- Incidents: Cross-tenant impact dropped to zero after per-tenant queues.
- Costs: +18% infra cost offset by predictable scaling and upsell to higher concurrency plans.
- SLA: Hit 99.95% by rate limiting webhooks at the edge and auto-scaling workers on queue depth.
- Security: Externalized secrets to KMS; passed a customer’s vendor risk assessment without extra pen testing delays.
Common Pitfalls (and Fixes)
- Pitfall: One big Redis and Postgres schema for everyone. Fix: Namespace queues and schemas; RLS if you must stay shared.
- Pitfall: Public webhooks without auth. Fix: JWT or HMAC, strict TTLs, and replay protection.
- Pitfall: Over-privileged egress. Fix: Per-tenant network policies; explicit allowlists.
- Pitfall: Manual upgrades. Fix: Canary channels with automated health checks and workflow snapshotting.
Quick Checklist
- Per-tenant DB schema and queue
- Gateway with JWT/HMAC + rate limits
- KMS-backed secrets, rotation, and audit
- RBAC + SSO, least privilege
- Observability with tenant tags
- Autoscale workers on queue depth
- Canary upgrade lanes and rollbacks
Wrap-Up Multi-tenant n8n isn’t magic — it’s discipline. Pick the isolation that matches your risk, enforce it everywhere (DB, queues, storage, network), and automate the boring parts: secrets, upgrades, and scaling. You’ll earn trust with security and keep it with reliability.
Read the full article here: https://medium.com/@sparknp1/safe-by-design-n8n-for-saas-multi-tenant-automation-that-scales-007b0bb63734